Cryptography
I created this page so that I can share what I'm learning in my latest pursuit: cryptography. I am particularly interested in the cryptanalysis end of it. I am slowly expanding my understanding of this artform, but it does have a pretty steep learning curve. I think that my background in both programming and security will greatly help. I will attempt to use as standard as notation as possible, but I am self-taught so I'm sure that the language will not be perfect. I plan to start the entries here (from the bottom) at a basic level and then work up to more advanced stuff. In this way, newcomers will hopefully be able to follow along as I progress (and hopefully they do as well). I am still a beginner at this and would appreciate any corrections or advice.
Crypto Basics
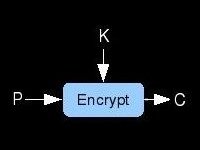
Learn about the very basics of cryptography. What does encryption mean? How are ciphers categorized? What uses does
crypto have other than scrambling messages? How can you sign a letter without a pen? I attempt to answer these sorts of questions on this
page. It is really for the beginners but it'd be cool if the experienced folks checked out gave me tips on how to improve it.
Block Ciphers
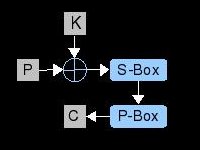
Discussed on this page are some of the elements used in the design of block ciphers. Also we examine two structures to combine these
elements into a full algorithm. Much of the vocabulary that will be used in later pages is explained here. Learn about s-boxes, key schedules,
linear mixing, and feistel ciphers and let me know what you think.
Cryptanalysis 101
Here we have a relatively non-technical overview of what cryptanalysis is. Known-plaintext attacks, frequency analysis, linear and differential
attacks, and more is discussed.
Linear Cryptanalysis Tutorial
After banging my head on the desk for 2 weeks, I finally found the bug in my LC code. On this page, I've explained as simply as I can how
a barebones linear attack would work on a 2-round 4-bit block cipher. We'll explore finding linear approximations, what the hell a linear
approximation is, and how to leverage them to break the cipher with less computational work than brute force. I haven't seen another page on
the net that walks the reader through the process and provides source code to play with. If you know of a page/paper about linear cryptanalysis
that doesn't require a math degree to understand, please let me know. In the meantime, enjoy this tutorial and, as always, let me know what you
think.
Differential Cryptanalysis Tutorial
Here's another modern statistical attack applied to block ciphers. We'll use the classic differential attack to break a simple toy cipher and
recover the key in less than brute force time. We'll also explore how to find good differentials and use them to reduce the keyspace to be searched.
Enjoy and tell me your thoughts.
Multi-Round Differential Cryptanalysis
I had so much fun learning about DC while writing the last tutorial, I went a bit further with it here. The cipher attacked on this page is
quite a bit beefier. With a block size of 8 bits, 4 rounds, a P-Box, and a 32 bit key; its a hefty target. We'll chain several differential
characteristics together and find a chosen plaintext/ciphertext pair that satisfies this path. Next, we'll use the good pair and our path to
make assumptions about the hidden intermediate values in the cipher. These assumptions allow us to recover the key in far less time than
exhaustive search.
Differential Cryptanalysis of FEAL-4
This one is long as hell. We walk through a differential attack on the infamously weak FEAL-4 block cipher. Although being a favorite
cipher to beat on by the cryptography community, it is a real modern block cipher. Go slow, study the diagrams, read the code, and have fun.
Be sure to take this technique further and tell me about it so I can learn more. There is a ton of opportunity for improving the attack here.
Slide Attacks
Scaling back the difficulty a little bit here. This page describes a very basic form of slide attack. This technique is used to break
simple ciphers that attempt to rely on lots of rounds for their security against analysis. This, alone, is not enough and this page
will show you why.
Boomerang Attack on FEAL-6
This time we'll use an adaptive-chosen ciphertext technique called the boomerang attack to determine if a black box is running FEAL-6.
The boomerang attack was created to expand the power of differential cryptanalysis. Although, we will not be recovering any information
about the key, we will be identifying the algorithm inside just by feeding data into it. This distinguishing attack exploits 100% probable
differentials in FEAL and only requires 2 encryptions and 2 decryptions.
Impossible Differential Cryptanalysis
In this tutorial we'll check out yet another variant of the differential attack. We'll use the impossibility of differentials
injected by chosen-plaintext transforming into other differentials to break a toy cipher. By having certainty that a property
shouldn't exist at the input to the last round, we can make key guesses at the last-round subkey and rule out those subkeys when
the property appears. Narrow down the keyspace enough and you'll be left with the correct key.